
The cyber-threat landscape is always changing and evolving. Hackers are notoriously dynamic, constantly improving their tactics and tools to bypass the latest security countermeasures. Organizations that want to minimize their exposure to cyber threats need to be well-informed and up to date.
Because there is such a wide variety of digital threats, there’s no single solution when it comes to protecting yourself from a data breach. A comprehensive security strategy is required, complete with multiple layers of protection and detection.
With that in mind, what are the top cyber threats to your operation in 2021? Chances are, the following enemies are at your gate (if not already inside your walls):
1) Social Hacking
“Employees are still falling victim to social attacks. Financial pretexting and phishing represent 98 percent of social incidents and 93 percent of all breaches investigated,” says Securitymagazine.com.
This means that the largest risk of a data breach comes from within: your own staff. 93% of all the data breaches investigated in the year 2020 were traced back to a carelessly-opened email, malicious link, or other employee mishap. Most of these attacks were carried out through deliberate phishing (using phone emails to dupe employees), a method that remains extremely effective to this day.
To minimize your risk:
- Set a BYOD Policy. Bring-your-own-device (BYOD) policies establish rules and procedures for bringing personal devices into work. Such a policy can help limit the risks imposed by allowing personal computers, phones, and other devices onto the company network.
- Set Privilege Polices. Limit employee access only to resources necessary to perform their jobs.
- Raise Awareness and Provide Training. Training your employees to recognize common cybersecurity risks can go a long way toward securing your business. An employee who knows how to spot a phishing attempt is far less likely to click a malicious link or open a suspicious file.
2) Ransomware
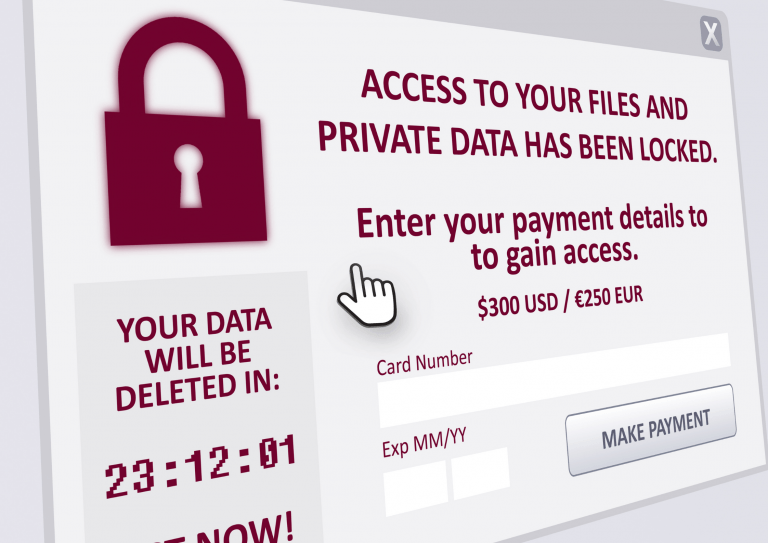
Businesses of all sizes are being increasingly targeted in Ransomware attacks.
These attacks use purpose-built malware to lock a business’ network and/or encrypt their data.
Once the Ransomware has done its work, it will display a message demanding payment from the business to restore access or decrypt the files. These demands are usually requested in untraceable Bitcoin, and paying the ransom doesn’t guarantee you’ll actually have your access restored.
You can reduce your Ransomware risk profile by:
- Educating Your Employees. Again, teaching employees to spot and avoid phishing attempts is a huge first step. (In most cases, Ransomware finds its way into a network via such emails.)
- Using Virus/Malware Scanning for Email Attachments. An automated system that scans emails and their links and attachments before they’re opened will reduce your risk considerably.
- Using Remote Data Backups. A cloud-based data backup can allow you to recover your lost data by reformatting the corrupted data storage drives and restoring them from the backup. Be sure to involve Cyber Security professionals at this point to ensure that the Ransomware is completely removed before restoring.
3) Unpatched Vulnerabilities/Poor Updating
Many common threats target known security bugs in popular business software programs. Even though many of these vulnerabilities already have fixes, they don’t work unless the patches are applied in a timely manner.
Create and adhere to a comprehensive patching schedule to limit your exposure to these threats. Any out-of-date software should be patched to the latest security version as soon as such patches become available. You should also actively check for security patches or software updates at least every 2-3 weeks.
We recommend against using software that is no longer supported by the developer, as this typically means even known vulnerabilities will not be addressed.
4) Distributed denial of service (DDoS) Attacks
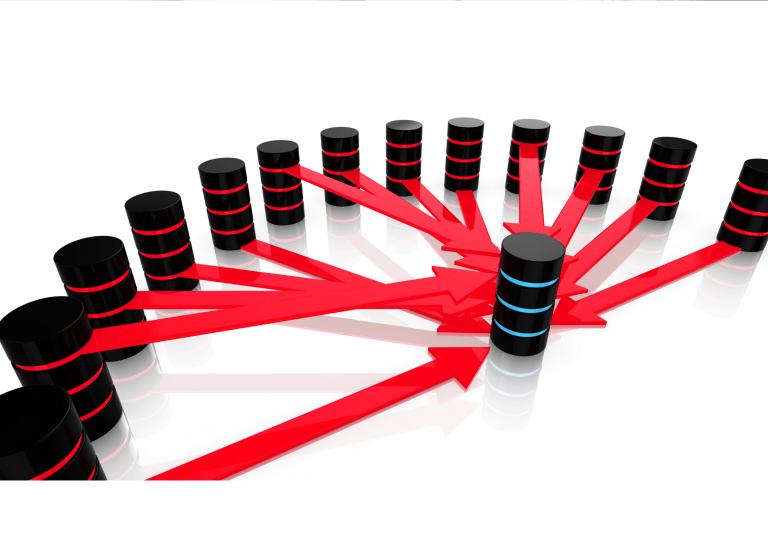
This type of attack overwhelms a victim’s network resources so they cannot process legitimate traffic.
Distributed denial of service (DDoS) attacks are worrisome for two reasons. First, they can curtail your ability to access your data, slow your network to a crawl, or shut down your public-facing website. Secondly, DDoS attacks are often used to conceal other malicious behavior. Behind the smoke screen of a DDoS attack, hackers will often attempt more serious data breaches.
There are a number of different means by which a DDoS attack can be carried out, which makes it challenging to thwart them. Doing so requires a comprehensive cybersecurity strategy that considers different kinds of DDoS threats, your available resources, and how to best counter specific DDoS attack types.
In most cases, enlisting the help of a specialized cybersecurity provider is the best option when DDoS attacks are occurring or expected.
Want to protect your business network from all of the cybersecurity threats on this list? Contact DigitalSafe Limited today to learn more about how we can help.
